Bug Bounty Program, the retrospective
When hunters make your business safer!
For several months, we experimented a Bug Bounty Program with the YesWeHack platform. Here is a retrospective, explaining why we did it, and what happened during this period.
Private program
The security of software cannot be assessed unless it is tested by a lot of hunters.
PrestaShop relies on a lot of dependencies, with hundreds of thousands lines of code, and this has been true since the very first versions.
We considered that publishing a public program, available for all, in the first place was risky as it could bring a huge volume of duplicated reports and create frustration among hunters. That is why we chose a private program first.
The benefit of the private program is to limit the number of hunters and manage the reporting flow. For each reported security issue, resources must be dedicated to understand it, reproduce it, build a patch, test the patch by the QA Team, etc. This can be quite expensive, so it is important to be able to adjust how many issues are reported thanks to the private program settings.
The process can appear quite slow and boring but it is nevertheless necessary to leave no room for doubt.
Public program
After a few months running this private program, we noticed the number of reports had decreased significantly. We finally released the program to the public on the 23rd of July 2020.
We thought that the public opening would bring in a huge volume of new reports, but this did not happen to our great surprise. It seems the hunters who participated in the private program helped us fix a large majority of security issues.
At the time we write this article, only one report submitted after the opening of the program to the public has been validated.
The big aim of having a Bug Bounty Program in public is to show everyone, and particularly our community, that our software can be trusted. We know it is secured because it has been tested by dozens of hunters and will be continuously tested by new hunters.
Some statistics
At the opening in March, more than 70 hunters were invited to the program.
Since then, we received a total of 98 reports
- Invalid: 4
- Out of Scope: 6
- Informative: 26
- Duplicate: 17
- Won’t fix: 2
- Valid: 43
- CVSS Score average: 5.59
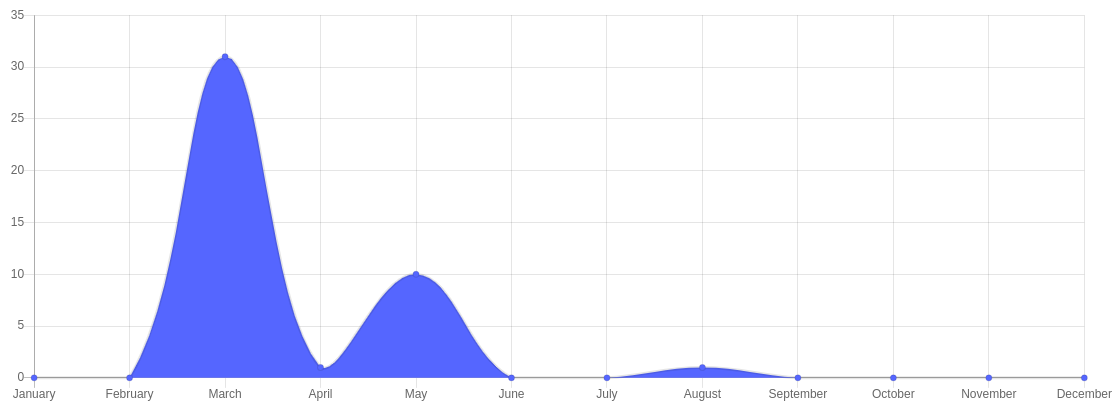
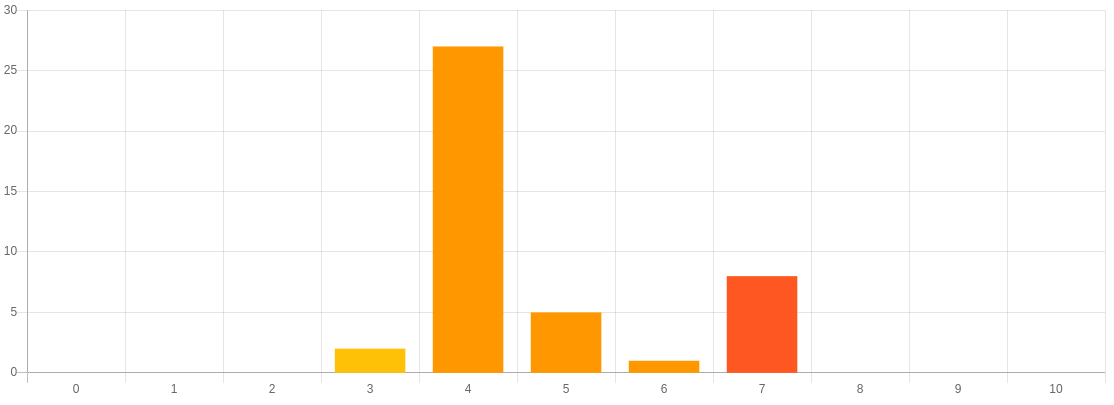
The following graphs cover the full period and highlight the reason why we decided to open the program to the public. Only valid reports are considered.
The graph below is a representation of the number of reports we received during the period.
Here is the representation of the CVSS3 Score results.
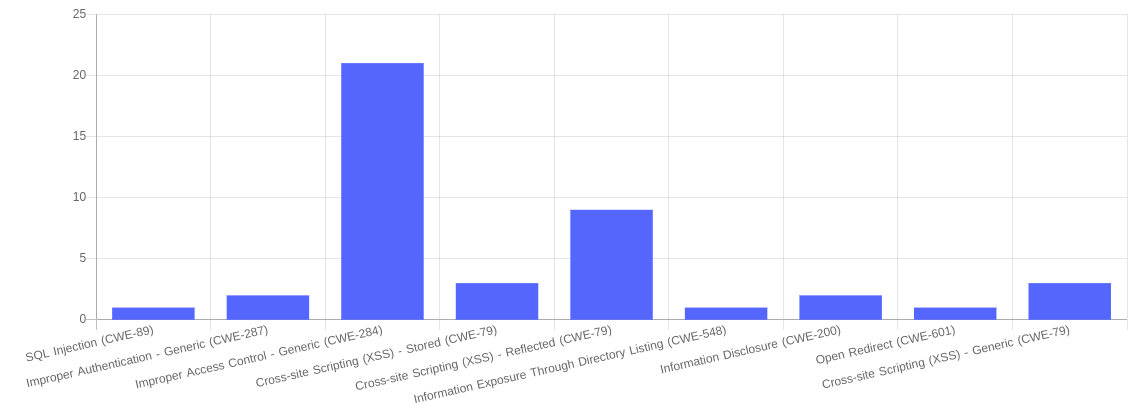
List of main vulnerabilities.
What’s next?
There is no plan to modify the program in the short term. For now, the Security team of PrestaShop continues to examine incoming bug reports with dedication. We are quite happy to use YesWeHack and the platform is really smooth, elegant and make the security reports easier to manage than our old security mailing list.
For next release, hunters will be notified automatically, so we are waiting for you hunters on YesWeHack platform!